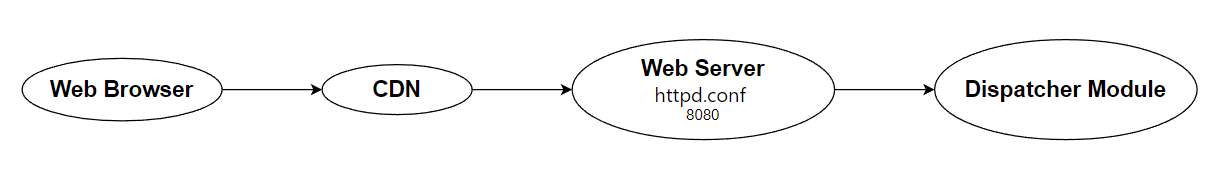
• First and foremost, we're understanding Web browser, CDN and website server which are isolated and operate together.
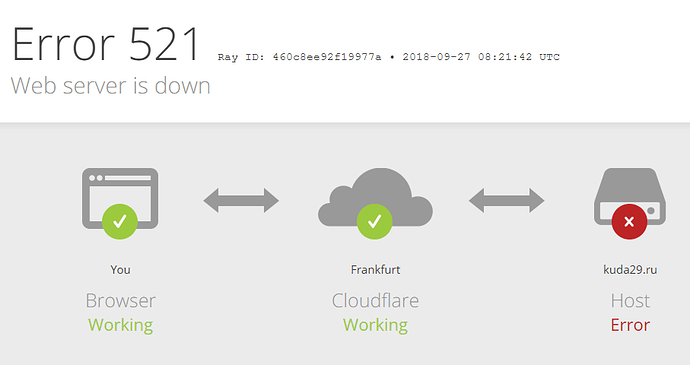
Here is common problem that happens upon connections interrupted. That means simple graphic was borning from above example:
You can visit link here to see ServerRoot and Port listen from website server.
ServerRoot "/usr/local/opt/httpd"
Listen 8080
• Dispatcher Module - Dispatcher is Adobe Experience Manager's caching and/or load balancing tool. Dispatcher also helps to protect your AEM server from attack and run as part of website server.
Based on web server's ability to serve static content. The Dispatcher stores cached documents in the web server's document root. There are two primary methods as
• Content Updates
• Auto-Invalidation
You can easily observe in ../available_farms/default.farm and ../enabled_farms/default.farm and the structure looks the following here:
/filter {
$include "../filters/filters.any"
}
# if the package is installed on publishers to generate a list of all content with a vanityurl attached
# this section will auto-allow the items to bypass the normal dispatcher filters
# Reference: https://docs.adobe.com/docs/en/dispatcher/disp-config.html#Enabling%20Access%20to%20Vanity%20URLs%20-%20/vanity_urls
# /vanity_urls {
# /url "/libs/granite/dispatcher/content/vanityUrls.html"
# /file "/tmp/vanity_urls"
# /delay 300
# }
# allow propagation of replication posts (should seldomly be used)
/propagateSyndPost "0"
# the cache is used to store requests from the renders for faster delivery
# for a second time.
/cache {
# The cacheroot must be equal to the document root of the webserver
/docroot "${DOCROOT}"
# sets the level upto which files named ".stat" will be created in the
# document root of the webserver. when an activation request for some
# handle is received, only files within the same subtree are affected
# by the invalidation.
/statfileslevel "2"
# caches also authorized data
/allowAuthorized "0"
# Flag indicating whether the dispatcher should serve stale content if
# no remote server is available.
/serveStaleOnError "1"
# the rules define, which pages should be cached. please note that
# - only GET requests are cached
# - only requests with an extension are cached
# - only requests without query parameters ( ? ) are cached
# - only unauthorized pages are cached unless allowUnauthorized is set to 1
/rules {
$include "../cache/rules.any"
}
# the invalidate section defines those pages which are 'invalidated' after
# any activation. please note that, the activated page itself and all
# related documents are flushed on an modification. for example: if the
# page /foo/bar is activated, all /foo/bar.* files are removed from the
# cache.
/invalidate {
/0000 {
/glob "*"
/type "deny"
}
/0001 {
/glob "*.html"
/type "allow"
}
# to ensure that AEM forms HTMLs are not auto-invalidated due to invalidation of any other resource. It is supposed to be deleted only after its own activation.
/0002
{
/glob "/content/forms/**/*.html"
/type "deny"
}
}
Adobe Experience Manager as a Cloud Service uses AEM Publish Dispatcher filters to ensure only requests that should reach AEM do reach AEM. By default all requests are denied, and patterns for allowed URLs must be explicitly added.
Hence, you need to define URL patterns allowed to reach AEM and must include the URL prefix for the AEM persisted query endpoint in ../filters/filters.any.
#
# This file contains the filter ACL, and can be customized.
#
# By default, it includes the default filter ACL.
#
$include "./default_filters.any"
# Allow components JSON model
/0101 { /type "allow" /extension "json" /selectors "model" /path "/content/*" }
# Allow manifest.webmanifest files located in the content
/0102 { /type "allow" /extension "webmanifest" /path "/content/*/manifest" }
# Allow user JSON
/0103 { /type "allow" /extension "json" /selectors "infinity" /path "/home/*" }
# Allow Your sites JSON
/0201 { /type "allow" /url "/bin/pdf/custom-statement" }
/0202 { /type "allow" /extension "json" /selectors "customstatement" /path "/content/*" }
In the other case, if you are using AEM with Touch UI you should not cache author instance content. If caching was enabled for the author instance, you need to disable it and delete the contents of the cache directory. Hence, we can disable those into ../cache/rules.any file.
#
# This file contains the cache rules, and can be customized.
#
# By default, it includes the default rules.
#
$include "./default_rules.any"
# Do not cache servlet calls
/0021 {
/glob "*.customstatement.json"
/type "deny"
}
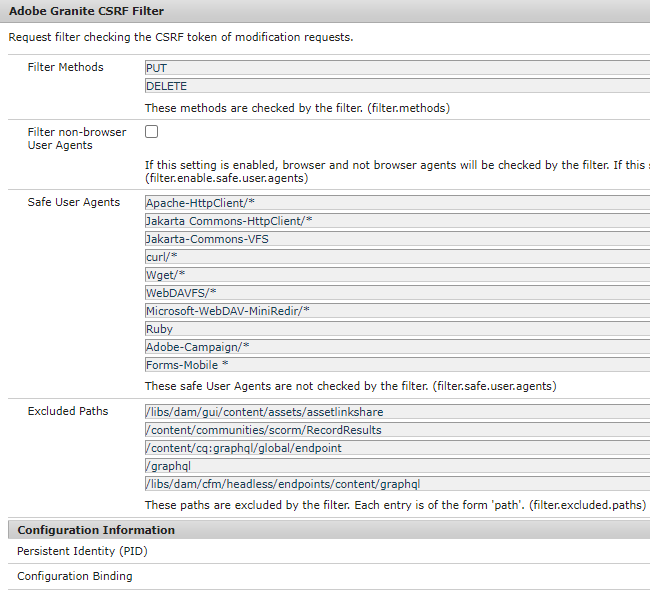
• Configuring Dispatcher to Prevent CSRF Attacks. AEM provides a framework aimed at preventing Cross-Site Request Forgery attacks. You can observe ../clientheaders/clientheaders.any in dispatcher module.
#
# This is the default list of request headers to forward to AEM.
#
# DO NOT EDIT this file, your changes will have no impact on your deployment.
#
# Instead modify clientheaders.any.
#
"X-Forwarded-Proto"
"X-Forwarded-SSL-Certificate"
"X-Forwarded-SSL-Client-Cert"
"X-Forwarded-SSL"
"X-Forwarded-Protocol"
"CSRF-Token"
"referer"
"user-agent"
"from"
"content-type"
"content-length"
"accept-charset"
"accept-encoding"
"accept-language"
"accept"
"host"
"if-match"
"if-none-match"
"if-range"
"if-unmodified-since"
"max-forwards"
"range"
"cookie"
"depth"
"translate"
"expires"
"date"
"if"
"lock-token"
"x-expected-entity-length"
"destination"
"Sling-uploadmode"
"x-requested-with"
"If-Modified-Since"
"Authorization"
"CSRF-Token" - CSRF is an serious attack in which a malicious third party (website, blog or a program) causes a authenticated users’ web browser to perform unwanted action on a trusted site. In some cases, we can remove POST/GET from Adobe Granite CSRF Filter in Felix console.