AWS IAM Identity Center makes it easy to manage workforce identities, control access, and integrate with popular identity sources for secure user authentication on AWS such as Microsoft Active Directory, Okta, Ping Identity, Jump Cloud, Google Workspace, and Azure Active Directory (Azure AD).
I. Creating and configuring an organization
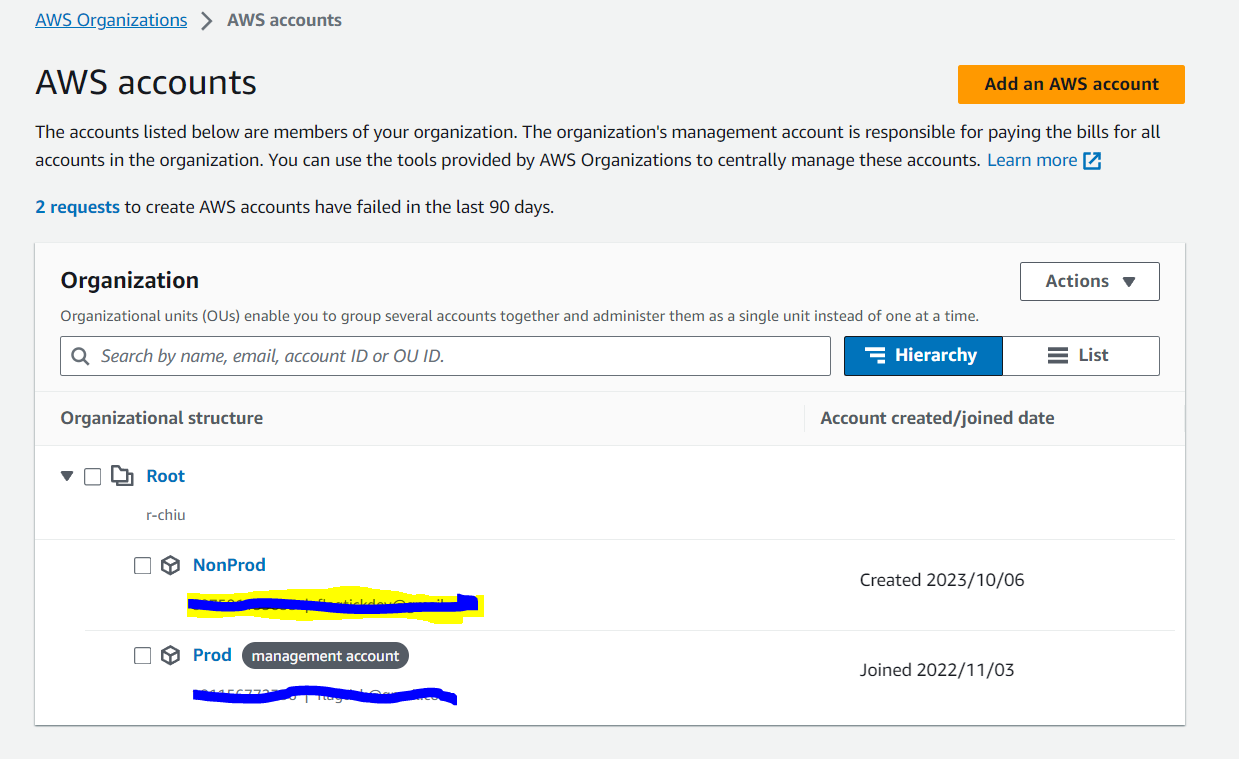
First and foremost, you need a root AWS account to access AWS Organizations and create new AWS accounts. From the caret icon in the top right corner, select your AWS account name and choose Organization.
The AWS Organizations console primarily provides tools for managing and organizing multiple AWS accounts within your organization, handling billing and cost management, and applying policies and controls to AWS accounts.
Use Prod (Production) and NonProd (Non-Production or Development) pattern is a common and simple approach to manage resources for team development. AWS Accounts play a role in granting specific access and privileges to a group of services for each assigned user or environment, such as development, staging, and production.
Additionally, we have other examples:
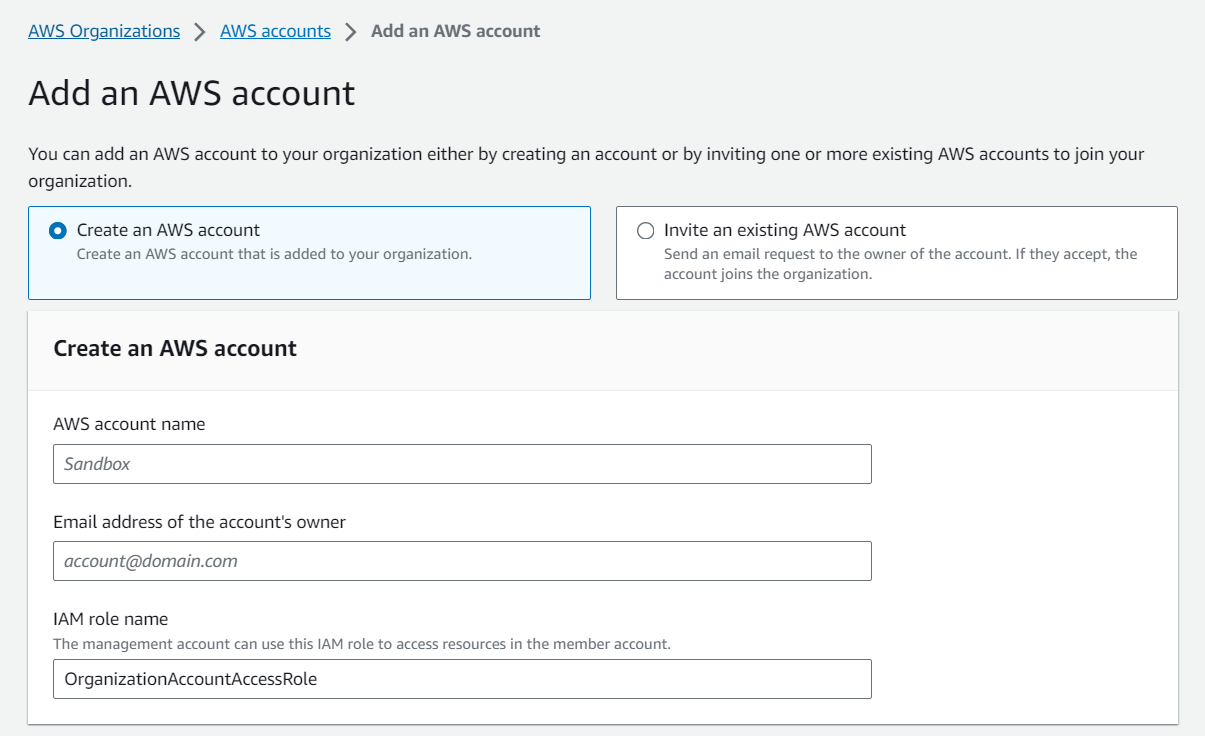
The next step is to set up an AWS Organization Account which comes along with an email for the organization.
After creating your AWS account, you can open the IAM Identity Center by searching for it in the AWS Management Console dashboard.
II. AWS IAM Identity Center
In the AWS Management Console, you can use the "Services" menu at the top to find and access IAM Identity Center (previous name is AWS SSO):
As you can see, the Amazon Resource Name (ARN) arn:aws:sso... indicates the AWS Single Sign-On service. There are a couple of pieces of information that you need to pay attention to:
- AWS access portal URL: https://d-9667753f44.awsapps.com/start
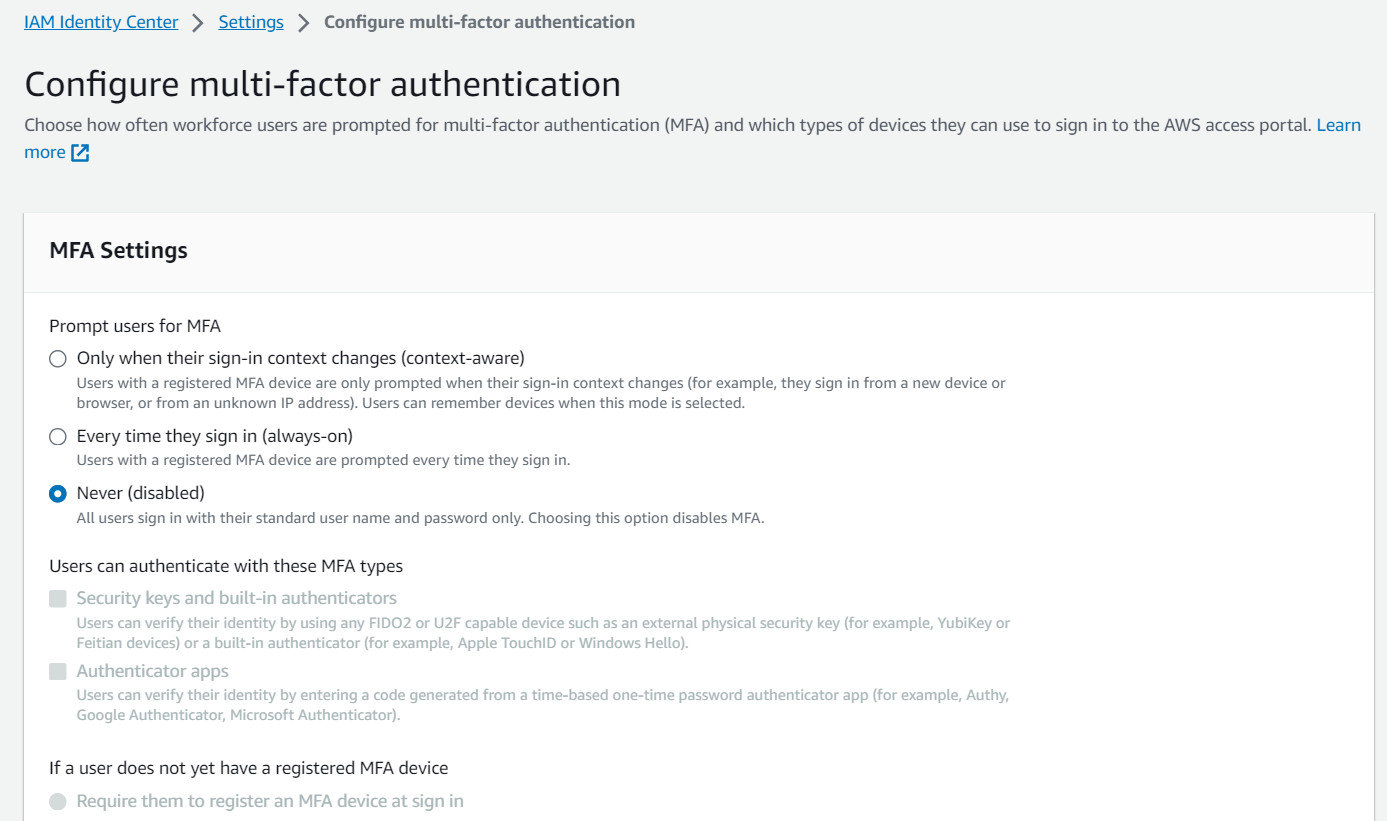
- Configure multi-factor authentication
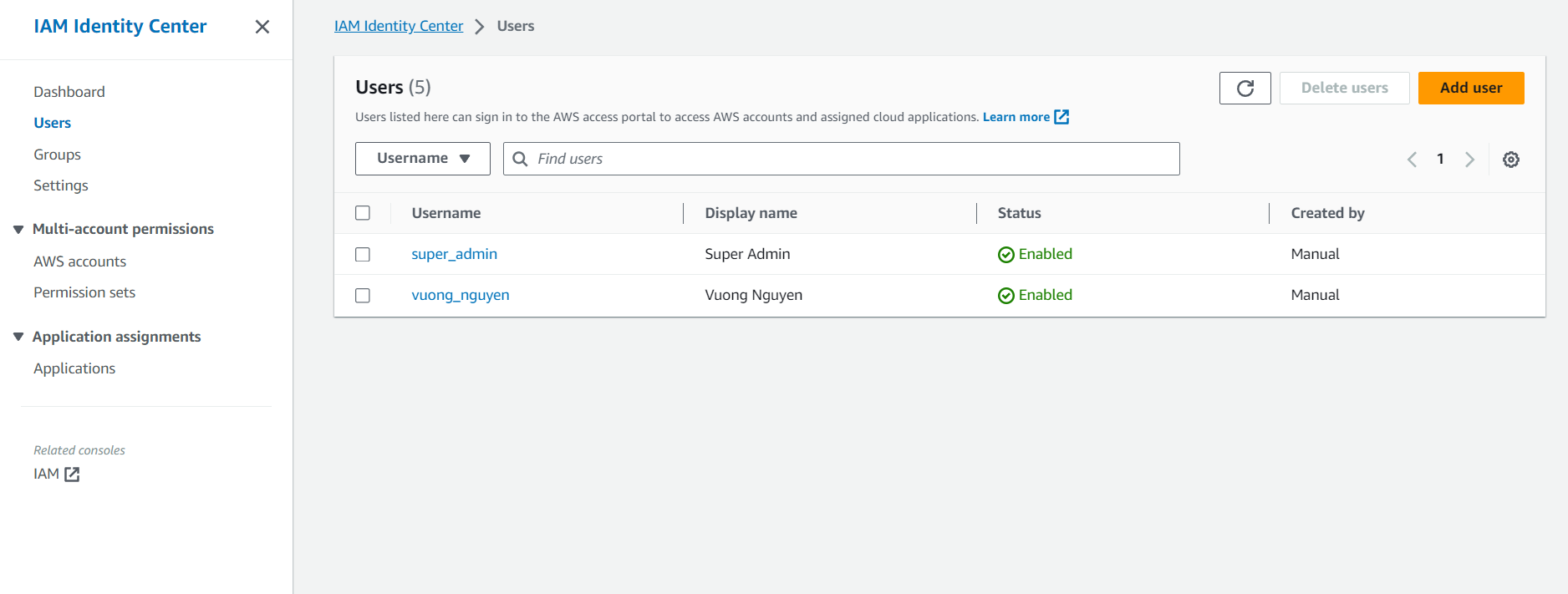
Navigating to Users tab, where you use the following procedure to add users to your Identity Center directory using the IAM Identity Center console.
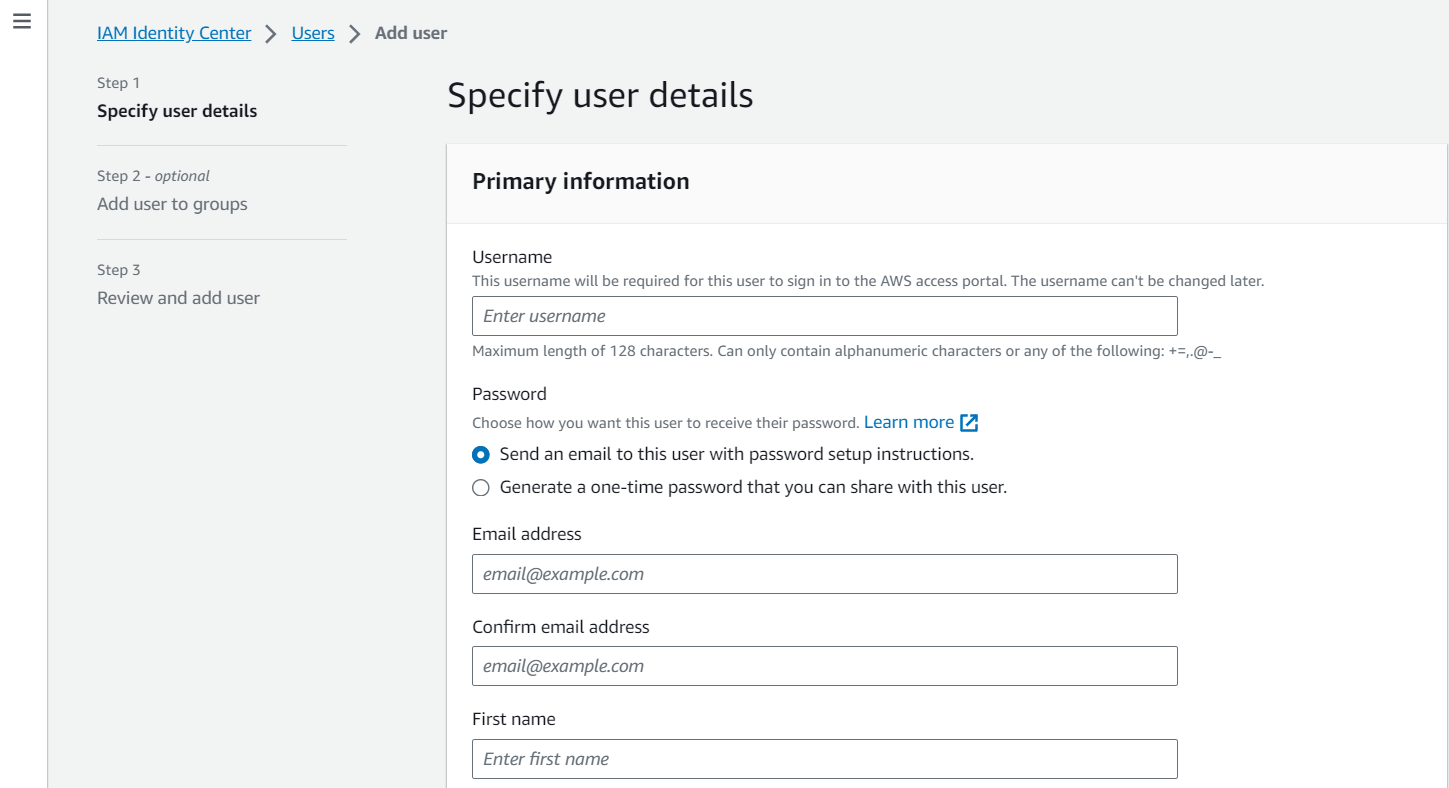
Click the Add user button in IAM Identity Center under Users to add a user, and then select the checkbox for Send an email to this user with password setup instructions. Once you click Next, an email will be triggered to be sent to the user, providing them with instructions on how to verify their identity (if necessary) and set up or change their password.
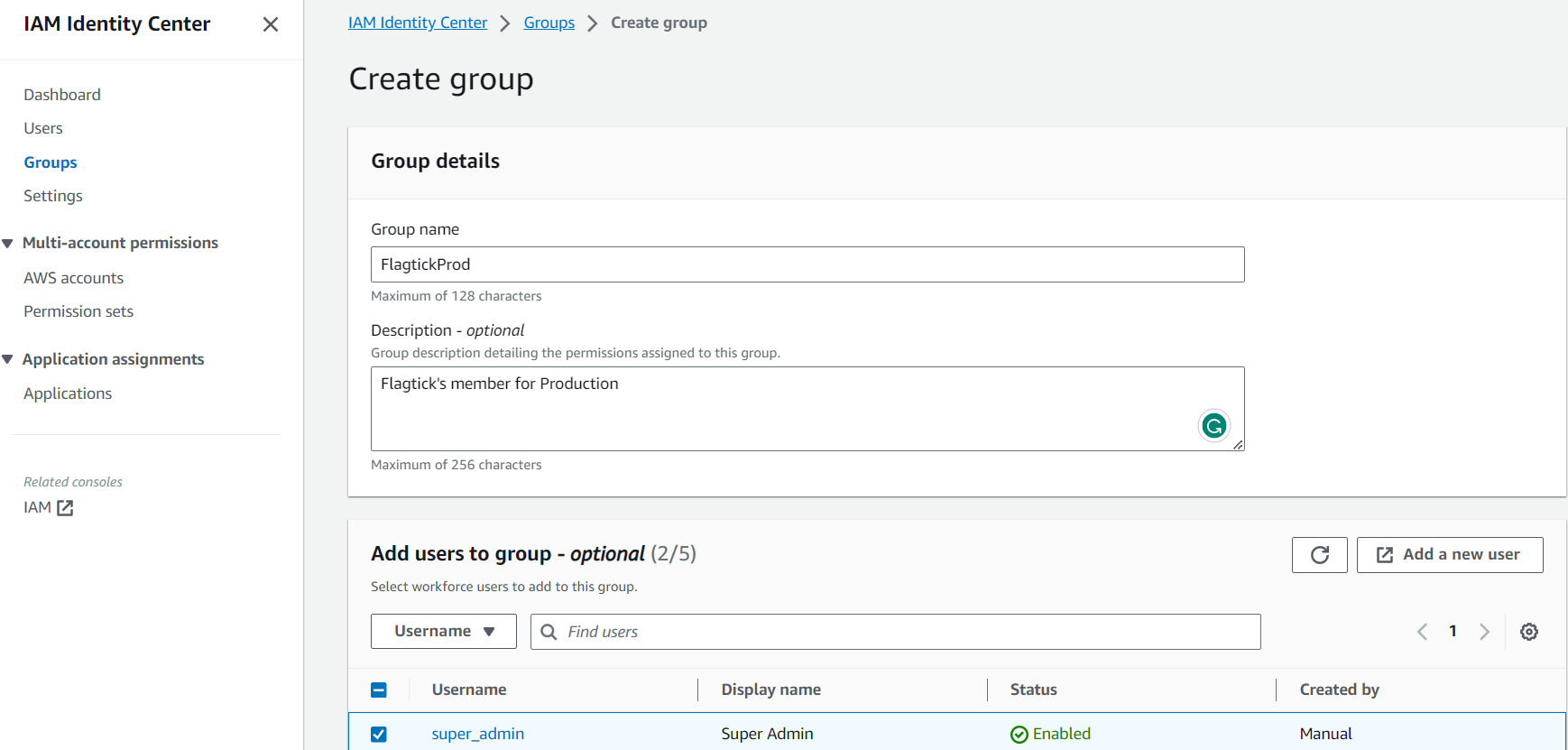
Similarly, for the Groups, you can follow the same steps. Create a sample group and add the users you previously added to the Users section.
You can create multiple groups to manage specific users with certain access to AWS services. Each group can be tailored to grant different access permissions to users as needed.
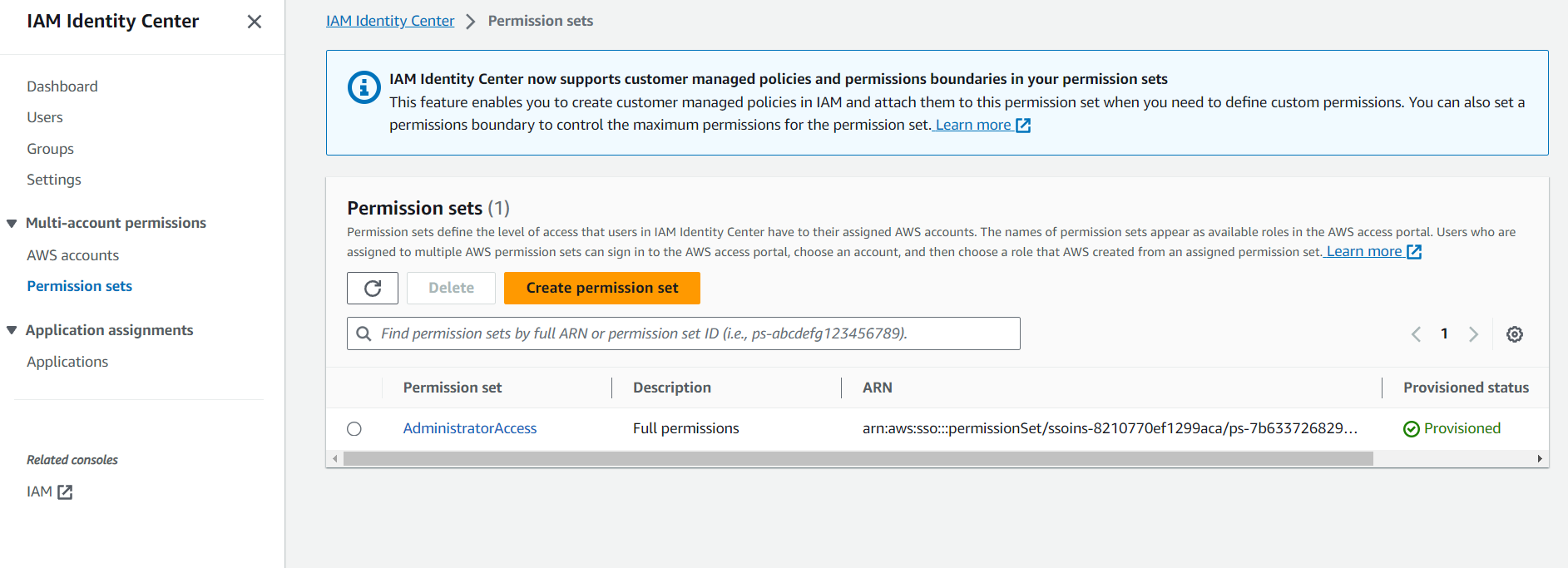
III. AWS Single Sign-On permission sets
By clicking on Permission sets, you gain direct access to the management and configuration of permission sets. This enables you to define and assign access rights and policies to users and groups within your AWS organization.
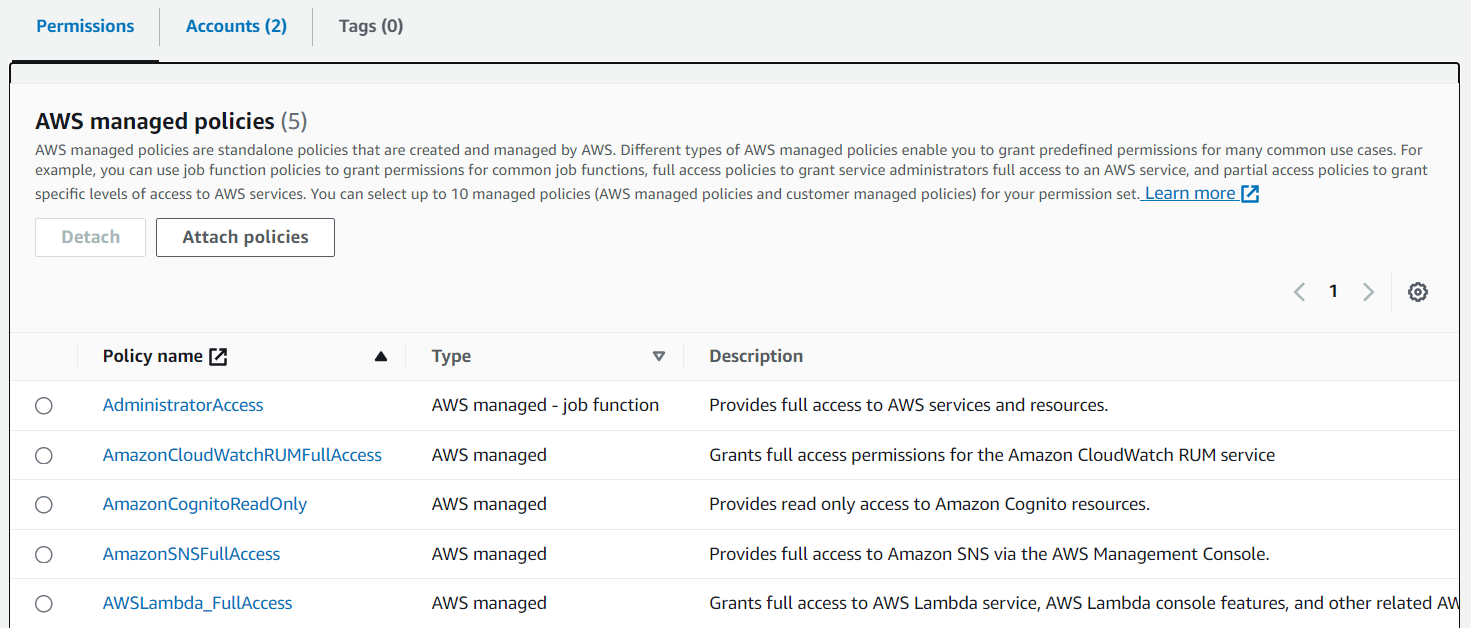
You can create a permission set named AdministratorAccess. This implies that you are integrating permissions from AdministratorAccess with full access. In the Permissions tab, you will find a list of permission types, including:
- AWS managed policies
- Customer managed policies
- Inline policies
- Permissions boundaries
You can leverage the AdministratorAccess permission set to grant full permissions, which allows you to add or modify permissions for AWS accounts.
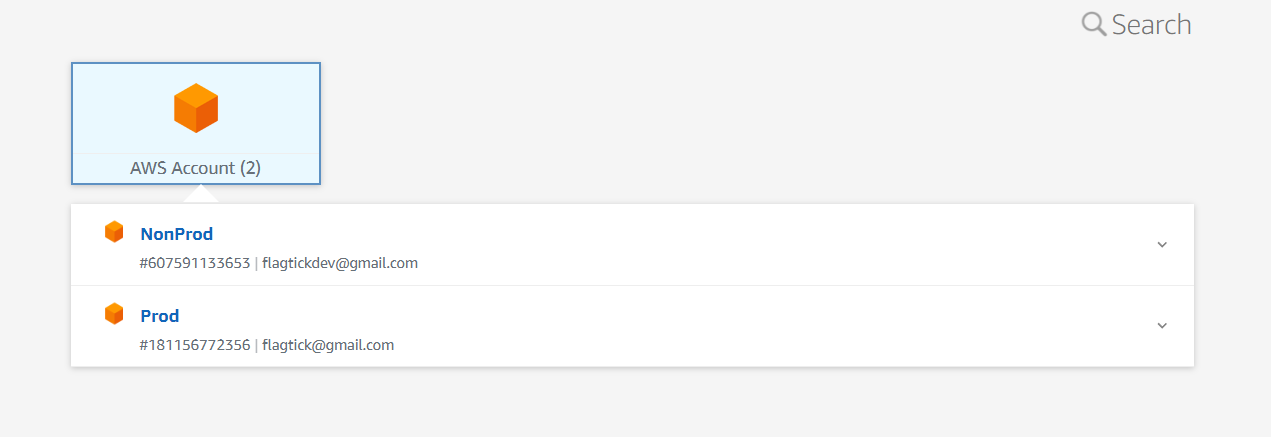
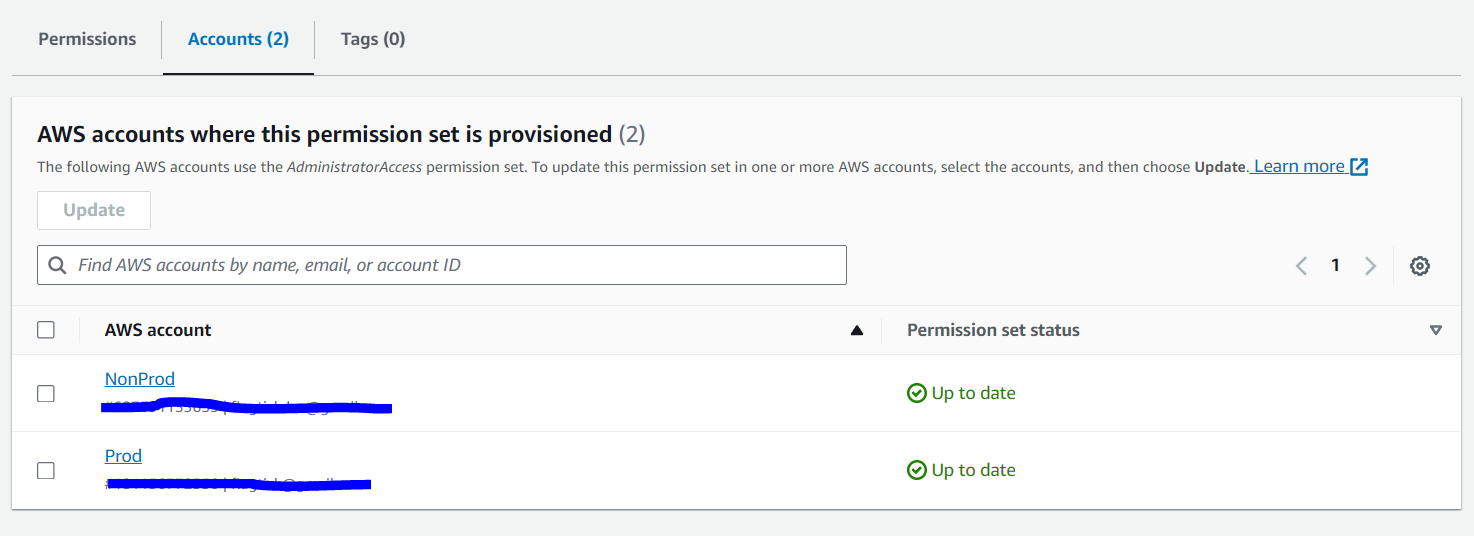
As you can see, we have already added the AdministratorAccess permission set to both the Prod and NonProd AWS accounts.
IV. Create and Attach Customer Managed Policies
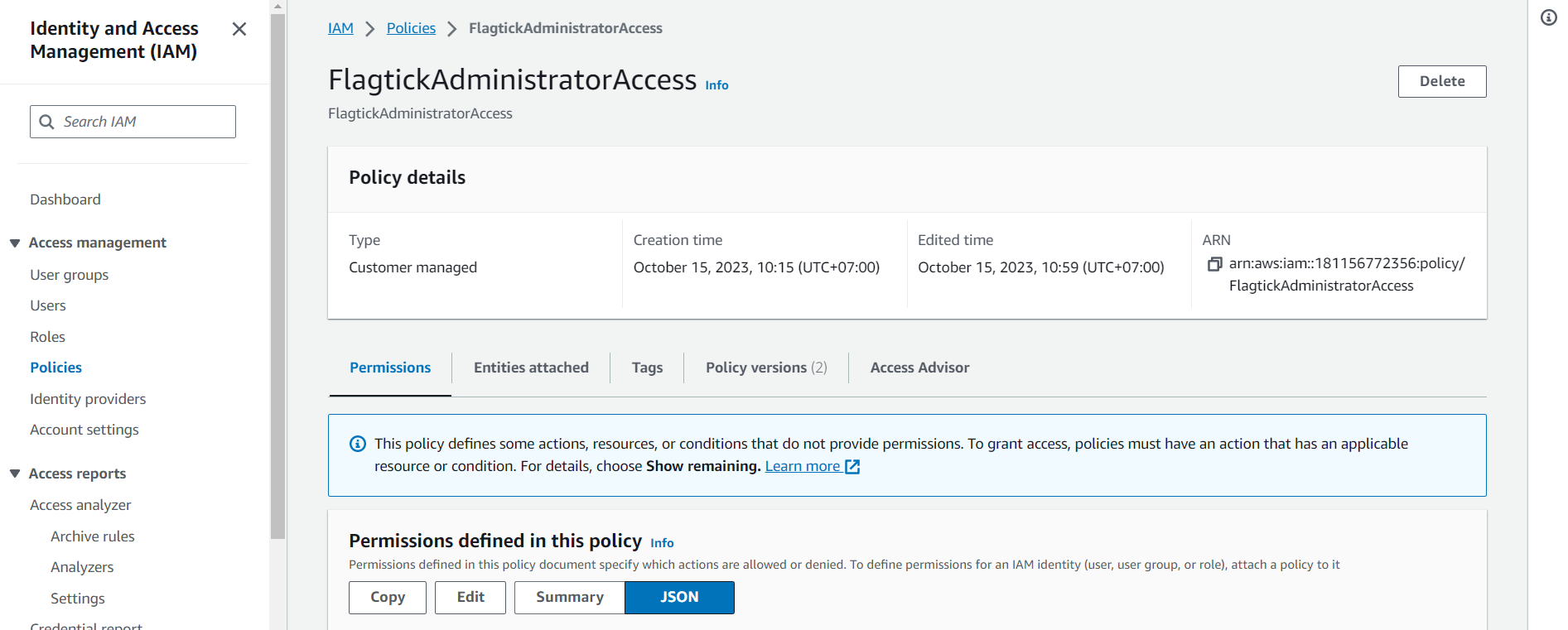
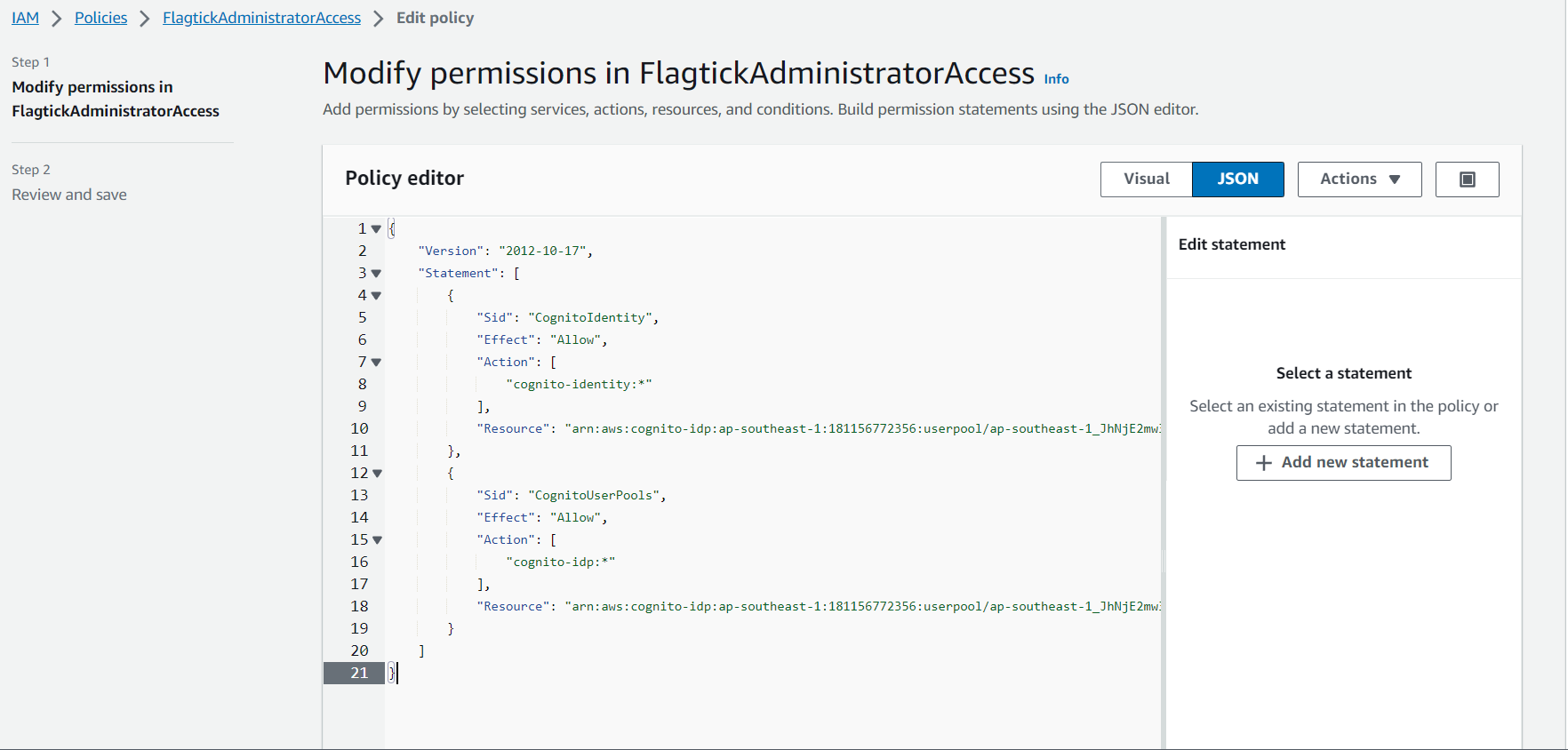
The purpose of creating and attaching customer-managed policies, which is to restrict or tailor user permissions based on policies associated with specific AWS services. Hence, let move on to navigate to the IAM console, go to Policies, and create a new policy.
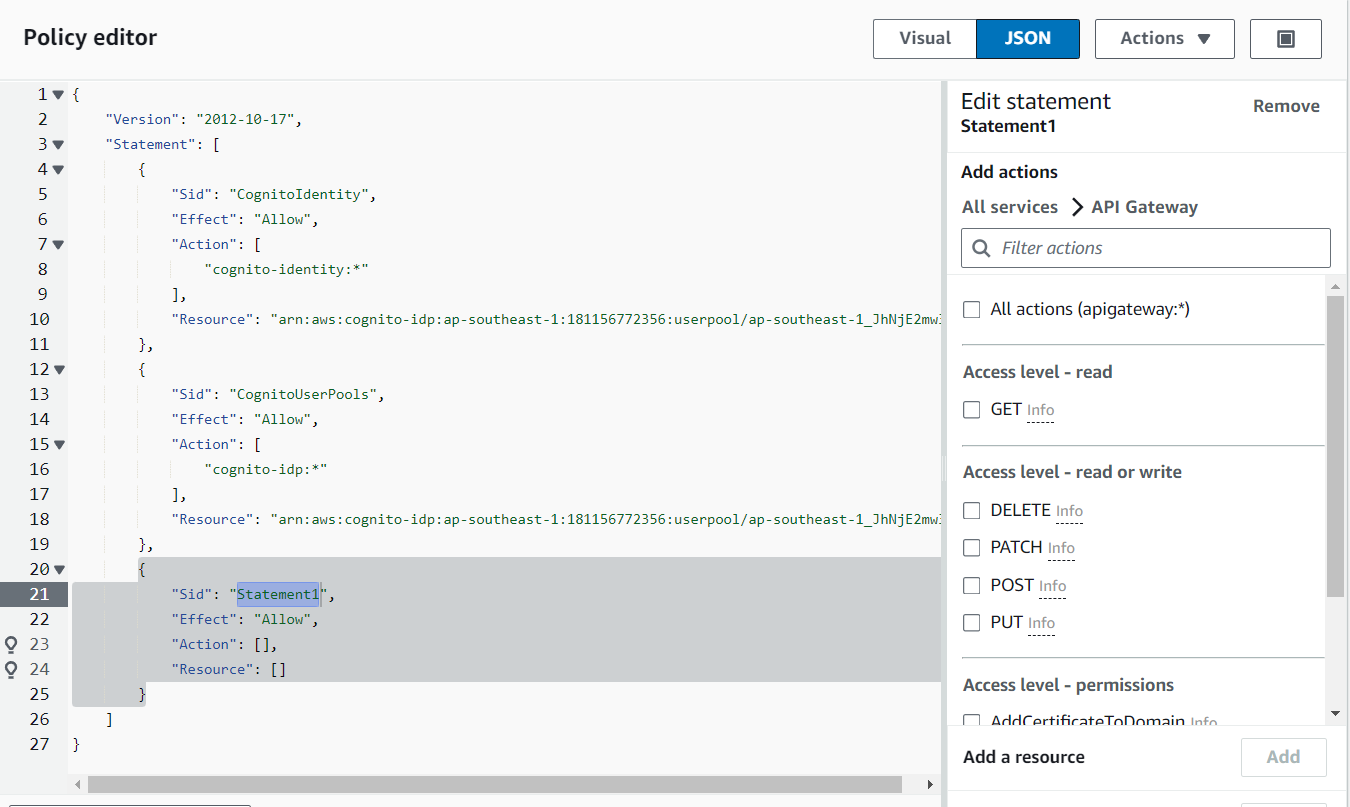
Clone the AdministratorAccess policy and rename it to FlagtickAdministratorAccess. Then, use the JSON editor to modify the policy's statements in detail to customize the permissions.
Select a statement to view a visual representation of the permissions and make any necessary modifications using the Policy editor.
After making the modifications, replace AdministratorAccess with FlagtickAdministratorAccess and proceed to add users to AWS accounts based on the updated settings.
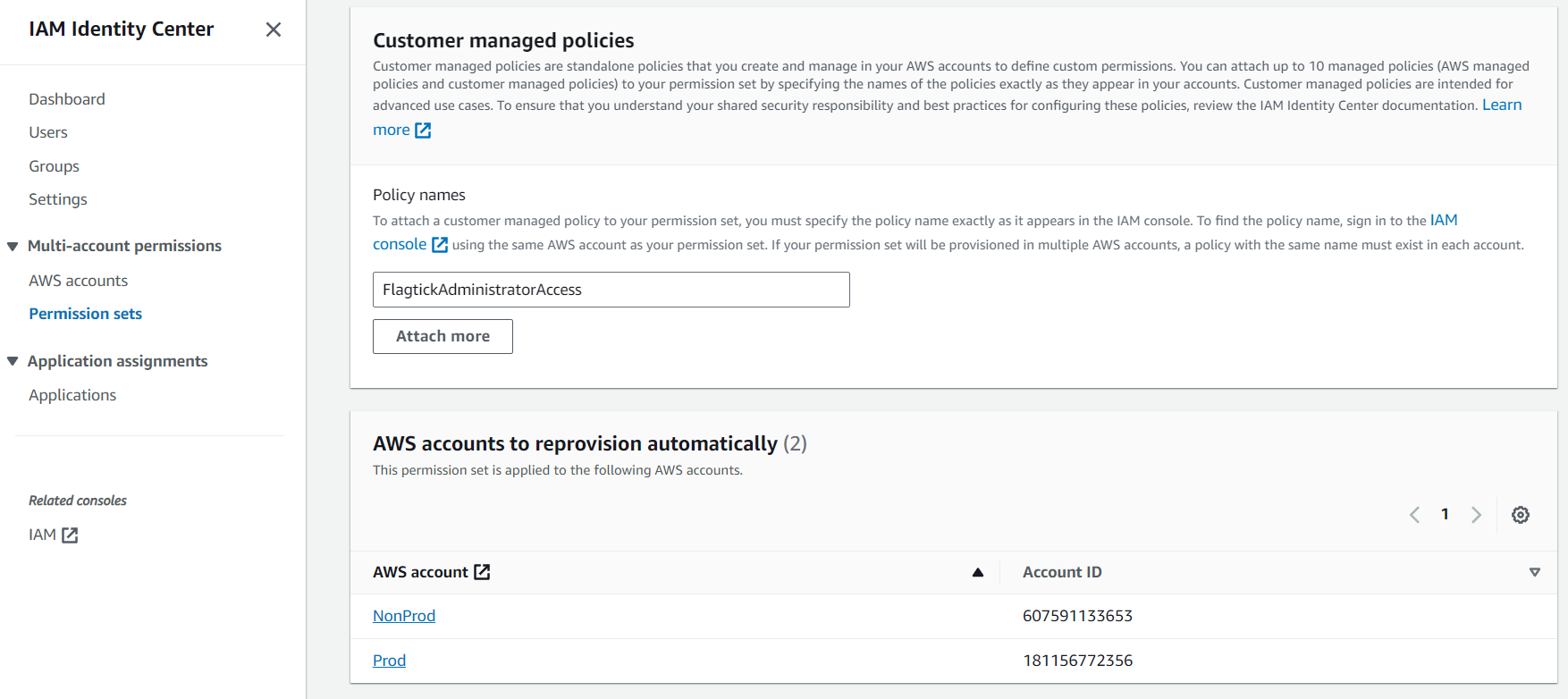
Please remember that you need to be logged in to your AWS Account to add a customer-managed policy to that AWS Account.
Note: If you want to add FlagtickAdministratorAccess to NonProd, you must log in to the NonProd AWS Account.
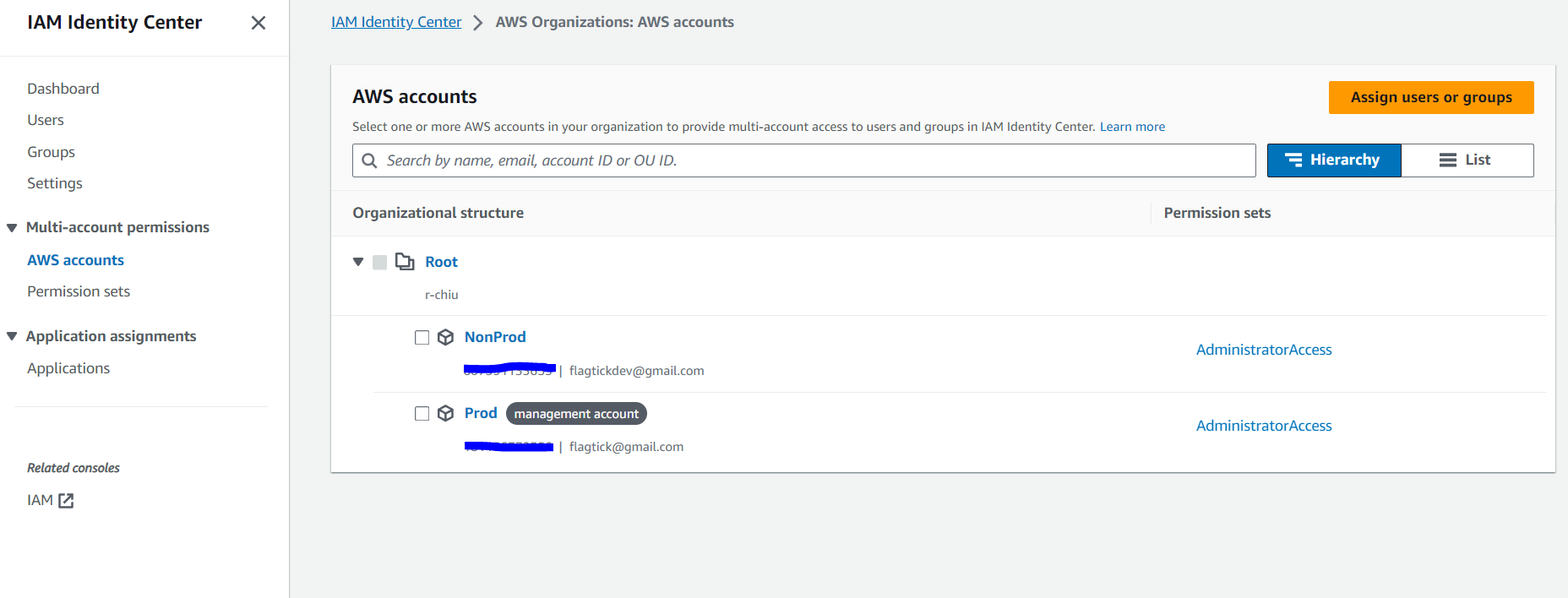
Now, go to AWS Accounts to view the AWS accounts in your organization. This allows you to provide multi-account access to users and groups in IAM Identity Center.
For example, if you want to add a user or group to the Prod AWS Account, you need to access the Prod AWS Account first.
Click Assign users or groups to add specific users or groups and grant them the AdministratorAccess permission set. As shown above, this permission set has already been added and can be viewed in the Permission sets column.
After configuring the FlagtickAdministratorAccess policy, you can log in with the username vuong_nguyen to check the access restrictions.
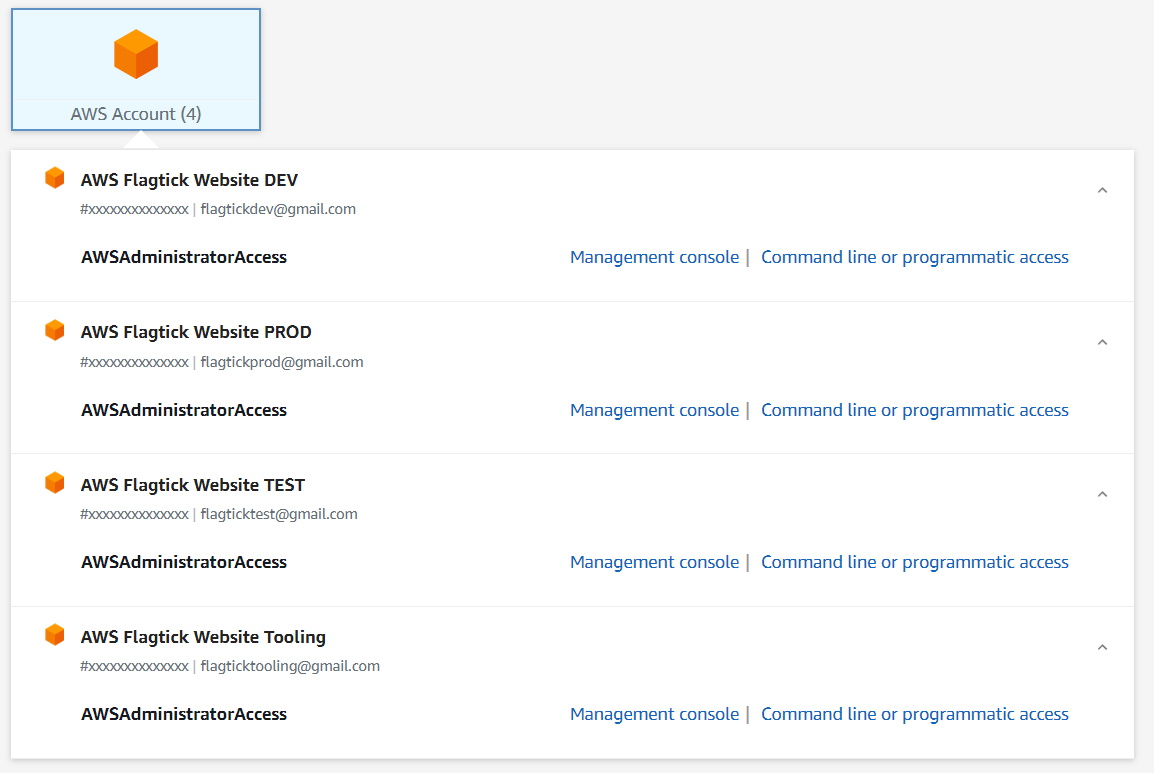
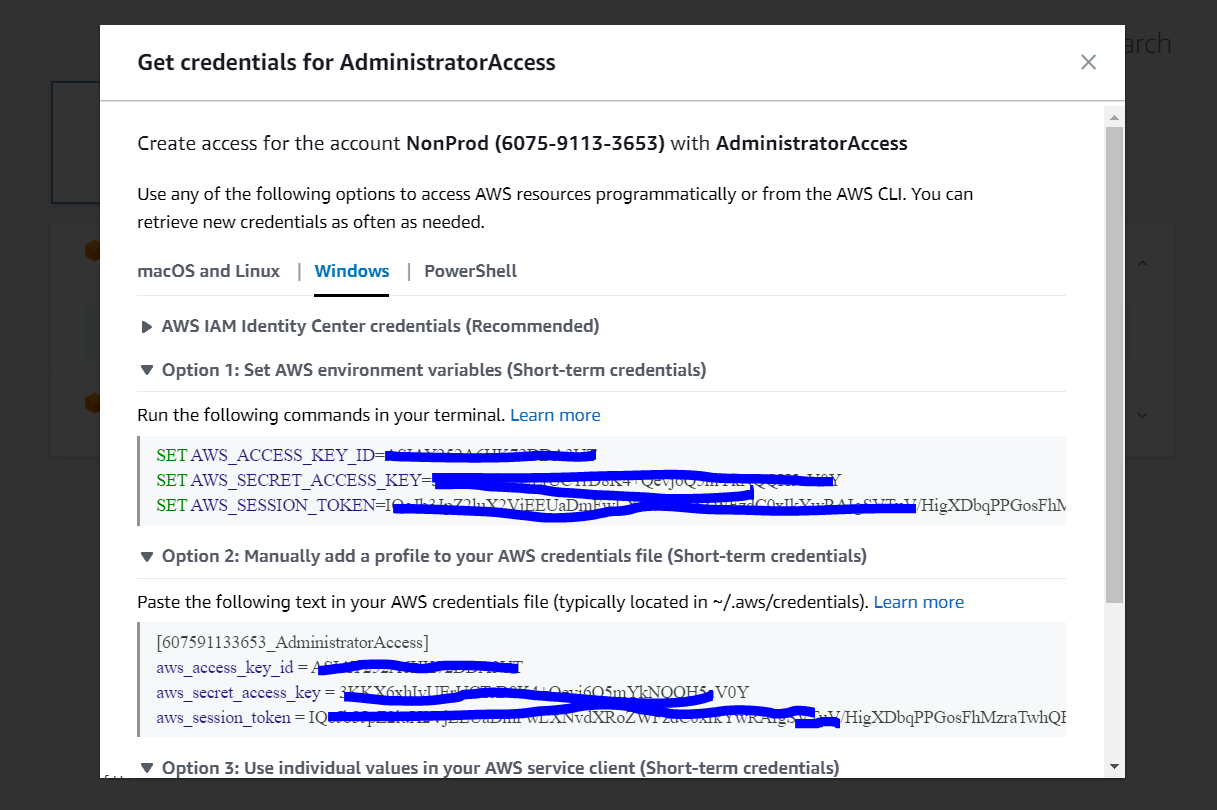
V. AWS IAM Identity Center credentials
Choose from the following options to programmatically access AWS resources or use the AWS CLI. You can obtain new credentials as frequently as necessary.
To do this, you'll need to install the AWS CLI on your local machine. Once installed, you can use it to perform various operations, such as listing all roles. For example:
C:\Users\admin>aws iam list-roles
{
"Roles": [
{
"Path": "/aws-reserved/sso.amazonaws.com/ap-southeast-1/",
"RoleName": "AWSReservedSSO_AdministratorAccess_d38ccc8540bd6107",
"RoleId": "AROAY252A6HK3UMAJU2NH",
"Arn": "arn:aws:iam::607591133653:role/aws-reserved/sso.amazonaws.com/ap-southeast-1/AWSReservedSSO_AdministratorAccess_d38ccc8540bd6107",
"CreateDate": "2023-10-15T04:05:13+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::607591133653:saml-provider/AWSSSO_1a310589cf538715_DO_NOT_DELETE" },
"Action": [
"sts:AssumeRoleWithSAML",
"sts:TagSession"
],
"Condition": {
"StringEquals": {
"SAML:aud": "https://signin.aws.amazon.com/saml"
}
}
}
]
},
"Description": "Full permissions",
"MaxSessionDuration": 43200
},
{
"Path": "/service-role/",
"RoleName": "resendConfirmationCode-role-f0dzdlw5",
"RoleId": "AROASULOI7ICGDKLXBF7K",
"Arn": "arn:aws:iam::181156772356:role/service-role/resendConfirmationCode-role-f0dzdlw5",
"CreateDate": "2023-10-14T07:51:04+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"MaxSessionDuration": 3600
}
-- More --
Sometime, The error message "An error occurred (AccessDenied) when calling the XXX Operation" typically indicates that the IAM user or role making the AWS API call doesn't have the necessary permissions to perform the specified operation. Let list all the managed policies attached to the specified role, including both AWS managed policies and customer managed policies.
C:\Users\admin>aws iam list-attached-role-policies --role-name resendConfirmationCode-role-f0dzdlw5
{
"AttachedPolicies": [
{
"PolicyName": "FlagtickProdCognitoIdentity",
"PolicyArn": "arn:aws:iam::181156772356:policy/FlagtickProdCognitoIdentity"
},
{
"PolicyName": "AWSLambdaBasicExecutionRole-ed90961b-60b1-4427-9927-6887c1f32d6c",
"PolicyArn": "arn:aws:iam::181156772356:policy/service-role/AWSLambdaBasicExecutionRole-ed90961b-60b1-4427-9927-6887c1f32d6c"
}
]
}
Next, view the JSON structure of an AWS IAM policy.
C:\Users\admin>aws iam get-policy-version --policy-arn arn:aws:iam::181156772356:policy/FlagtickProdCognitoIdentity --version-id v1
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "cognito-idp:AdminGetUser",
"Resource": "arn:aws:cognito-idp:ap-southeast-1:181156772356:userpool/ap-southeast-1_JhNjE2mw3"
}
]
},
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2023-10-14T14:15:03+00:00"
}
}
As you can see here, the XXX operation mentioned above is AdminGetUser. When working with services in AWS, such as Lambda, to handle user checks from Cognito, you will need to modify the policy for this case. For example:
const AWS = require('aws-sdk');
const cognitoIdentityServiceProvider = new AWS.CognitoIdentityServiceProvider({ region: 'ap-southeast-1' });
exports.handler = async (event) => {
if (event && event.email) {
const email = event.email;
const getUserParams = {
UserPoolId: 'xx-xxxxxxxx-x_XXXXXXX',
Username: email,
};
try {
// Add custom policy that allows the AdminGetUser action on IAM role: resendConfirmationCode-role-f0dzdlw5
// FlagtickProdCognitoIdentity -> IAM Center (permission set)
// IAM Role: resendConfirmationCode-role-f0dzdlw5 => FlagtickProdCognitoIdentity + Trust Policy
const userData = await cognitoIdentityServiceProvider.adminGetUser(getUserParams).promise();
const emailVerified = userData.UserAttributes.find(attr => attr.Name === 'email_verified').Value === 'true';
if (emailVerified) {
return {
statusCode: 200,
body: JSON.stringify('Email address is already verified.'),
};
} else {
const resendParams = {
ClientId: 'xxxxxxxxxxxxxxxxxxxxx',
Username: email,
};
await cognitoIdentityServiceProvider.resendConfirmationCode(resendParams).promise();
return {
statusCode: 200,
body: JSON.stringify('Confirmation code resent successfully'),
};
}
} catch (error) {
return {
statusCode: 500,
body: JSON.stringify(`Failed to check or resend confirmation code. Furthermore, you can view ${error.message}`),
};
}
} else {
return {
statusCode: 400,
body: JSON.stringify('Missing or invalid email parameter in the request.'),
};
}
};
Once you understand, let us move on to another case as below.
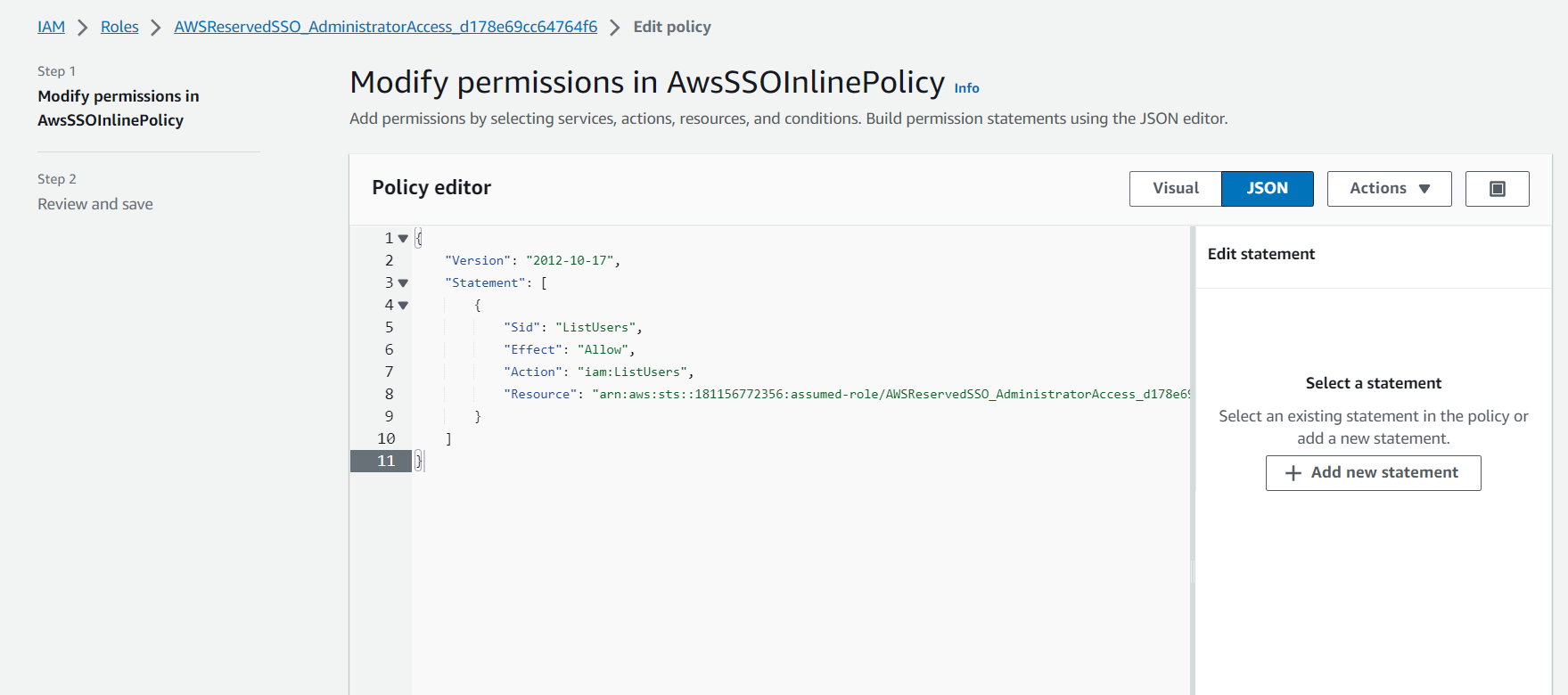
An error occurred (AccessDenied) when calling the ListUsers operation: User: arn:aws:sts::181156772356:assumed-role/AWSReservedSSO_AdministratorAccess_d178e69cc64764f6/vuong_nguyen is not authorized to perform: iam:ListUsers on resource: arn:aws:iam::181156772356:user/ because no identity-based policy allows the iam:ListUsers action
Make sure to notice the role named AWSReservedSSO_AdministratorAccess_d178e69cc64764f6 and the ListUsers operation.
VI. Conclusion
In this article, you'll learn how to set up and manage IAM Identity Center in AWS, which empowers you with centralized control over user access, strengthening security and compliance within your organization. Achieve a seamless IAM implementation by adhering to best practices and tailoring permissions to align with your unique needs.